Overview
Dropzone AI positions itself as an "AI SOC Analyst" platform that autonomously investigates security alerts to augment enterprise SOCs and MSSPs. The core goal is to automate Tier-1 investigations, remove investigator backlogs, reduce mean time to respond (MTTR), and leave human analysts to focus on higher-value work. The vendor claims typical investigations complete in roughly 3–10 minutes (with site references to "under 10 minutes" and some examples <20 minutes). The platform emphasizes evidence-backed reports, traceability and explainability of investigation steps. Key capabilities include multi-agent/LLM-based autonomous investigations with curated expert knowledge modules; an integrated chatbot for ad-hoc investigative queries tied to investigation context; automated data collection and correlation across many data and alert sources with categorized outcomes (Malicious, Suspicious, Benign) and detailed evidence; response automation and writeback to SIEMs/ticketing systems or remediators to trigger actions (for example device quarantine); Operational Context Memory for customer-specific facts to improve accuracy; and agent-driven investigations that do not require user-authored playbooks. The site lists roughly 70–85+ integrations spanning endpoints, cloud, identity, network, email, SIEM, SOAR, EDR, and threat intelligence, with example integrations named such as CrowdStrike, Microsoft Sentinel, Splunk, Google Workspace, AWS GuardDuty, Microsoft Entra ID, Microsoft Defender, VirusTotal, IPInfo and AbuseIPDB. Documentation (docs.dropzone.ai) contains per-integration configuration guides, remediator examples (e.g., Microsoft 365 remediator), connector guidance and admin topics (Okta SAML, metrics, connectors). Deployment is primarily a dedicated AWS tenant per customer (primary region noted as us-west-2) with optional in-region/EU deployments for data residency/GDPR, plus a lightweight on-prem connector (Docker) to access restricted systems without co-mingling data. The product is API-first with Swagger UI and API key support. Multi-tenant MSSP support is available with shared investigation capacity. Security and compliance notes on the site include SOC 2 Type II certification, annual third-party penetration testing (latest referenced December 2024) with no critical/high/medium/low vulnerabilities reported in that referenced test, tenant isolation, encryption in transit and at rest, role-based access controls (Administrator, Member, Restricted Read Only), and a stated policy that Dropzone does not train LLMs on customer data and contracts with LLM providers to avoid long-term storage of customer content. The platform emphasizes explainability, data lineage, QA and guardrails against hallucinations. Pricing calls out a starting figure of $36,000 per year per AI SOC analyst (including up to 4,000 full investigations annually) and notes enterprise, MSSP and custom pricing tiers; proof-of-concepts (POCs) are available. Support offerings list an 8-hour typical support SLA and roadmap/engineer access in plans. Documentation and resources include blog posts, solution briefs, webinars, case studies and self-guided demos. Named customers displayed on the site include organizations such as Indiana Farm Bureau Insurance, Zapier, Assala Energy, CBTS, Lemonade, OpenAI, Robinhood and Pangea Security. The site and docs appear actively maintained; some site links/pages may change or return 404s during restructuring.
Key Features
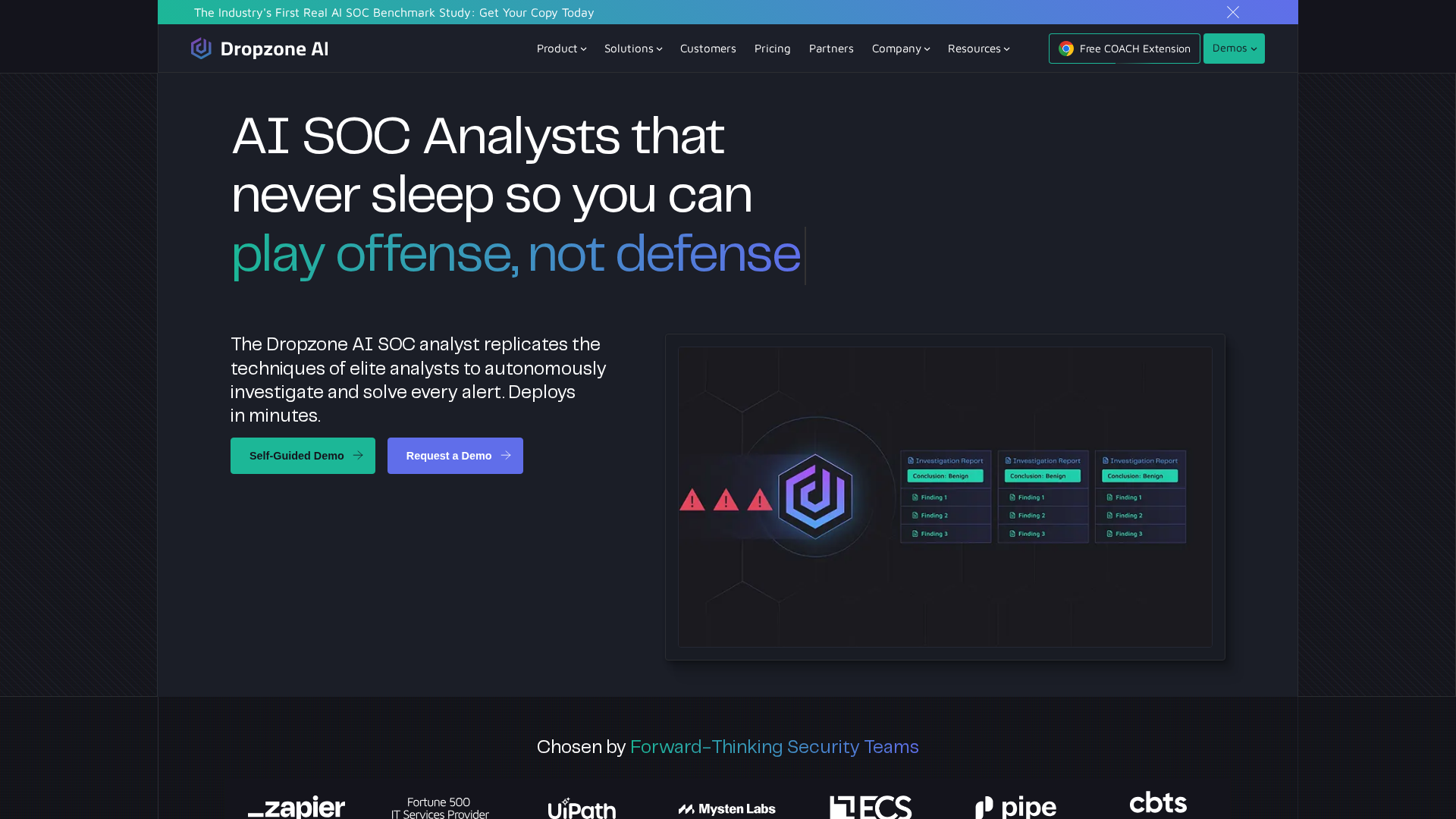
Autonomous investigations
Multi-agent / LLM-based reasoning with curated expert knowledge to autonomously investigate alerts and return evidence-backed outcomes.
Context-aware investigative chatbot
Interactive chatbot tied to investigation context for ad-hoc queries and follow-ups.
Data aggregation & correlation
Automatically gathers and correlates data from multiple data sources and alert sources and categorizes results (Malicious, Suspicious, Benign).
Response automation & writeback
Can post results back to SIEMs/ticketing systems or trigger remediators and custom workflows (e.g., quarantine devices).
Operational Context Memory
Stores customer-specific facts (IP ranges, hosts, roles) to improve investigation accuracy and contextual decisions.
Broad integrations coverage
70–85+ integrations across endpoints, cloud, identity, network, email, SIEM, SOAR, EDR and threat intelligence with per-integration docs.
Who Can Use This Tool?
- Enterprise SOCs:Scale Tier‑1 investigations, reduce backlog, enable 24/7 autonomous triage and response.
- MSSPs:Offer shared investigation capacity and multi-tenant operations to support multiple customers with automation.
- Lean SOC teams:Backfill historical alerts, automate common triage workflows and free analysts for higher-value tasks.
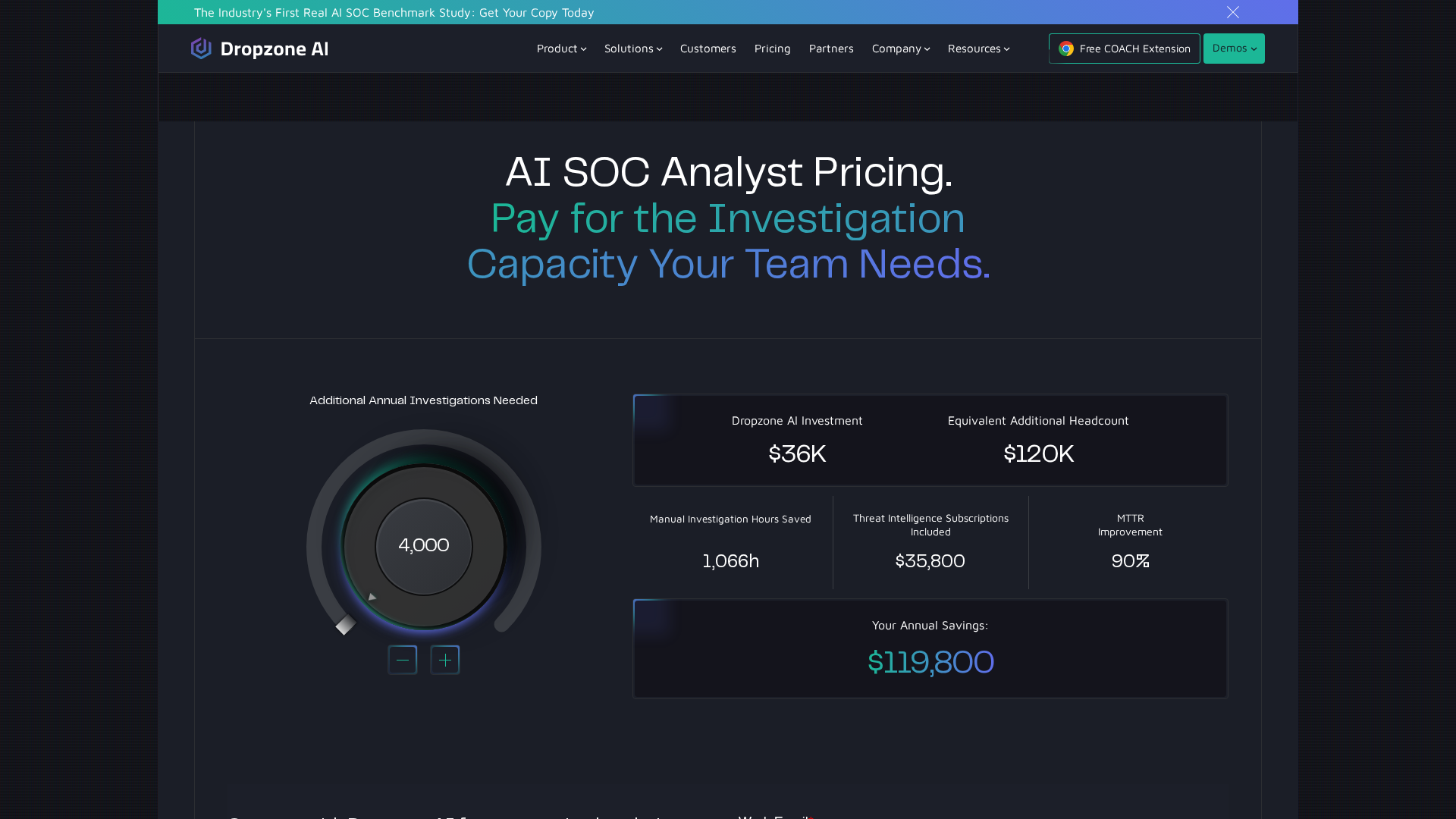
Pricing Plans
Annual subscription per AI SOC analyst; includes core automation and integrations.
- ✓Up to ~4,000 full investigations annually
- ✓Unlimited users (no seat limits)
- ✓Core automation and pre-built integrations
- ✓Curated threat intelligence feeds
- ✓AI chatbot and evidence-backed reports
- ✓8-hour customer support SLA, roadmap input and engineer access
Dedicated single-tenant environment with custom workflows and premium support (custom pricing).
- ✓Dedicated single-tenant environment
- ✓Custom workflows and integrations
- ✓Premium support and SLAs
- ✓Custom onboarding and professional services available
Multi-tenant MSSP offering with shared investigation capacity and premium SLAs (custom pricing).
- ✓Dedicated multi-tenant configuration for MSSPs
- ✓Shared investigation capacity
- ✓Premium SLAs and support
- ✓Custom pricing based on volume
Structured proof-of-concept engagements to evaluate capabilities before full deployment.
- ✓Time-boxed evaluation period
- ✓Integration and configuration support
- ✓Sample investigations and performance validation
Pros & Cons
✓ Pros
- ✓Autonomous, fast investigations with evidence-backed reporting and explainability.
- ✓Extensive integrations (70–85+), with per-integration documentation and remediator examples.
- ✓Deployment flexibility (dedicated AWS tenant, in-region/EU options, lightweight on-prem connector).
- ✓SOC 2 Type II and annual third-party penetration testing referenced; emphasis on tenant isolation and encryption.
- ✓Operational Context Memory and agent adaptability (no required playbooks).
✗ Cons
- ✗Pricing is relatively high (core figure $36,000/year per AI SOC analyst) and enterprise/MSSP pricing is custom.
- ✗Some public site pages may change or return 404s during site updates, indicating possible navigation/structure changes.
- ✗Limited public detail on complete pricing feature matrix and exact support SLA variations without contacting sales (POC or sales engagement needed).
Compare with Alternatives
| Feature | Dropzone AI | Radiant Security | Simbian |
|---|---|---|---|
| Pricing | N/A | N/A | N/A |
| Rating | 8.0/10 | 8.4/10 | 8.4/10 |
| Autonomous Investigations | Yes | Yes | Yes |
| Context Correlation | Yes | Yes | Yes |
| Response Automation | Yes | Yes | Yes |
| Traceable Reasoning | Partial | Yes | Partial |
| Integrations Coverage | Yes | Yes | Yes |
| Deployment Flexibility | Yes | Partial | Yes |
| SOC Workflow Builder | Partial | Partial | Partial |
Related Articles (4)
A hub of Dropzone AI's blog posts on AI-augmented security operations with use cases, tutorials, and benchmarks.
A compelling case for a cross-tool AI SOC analyst that links signals across tools to close investigations faster and more accurately.
A roundup of Dropzone AI in 2025: funding, Gartner hype-cycle insights, industry recognition, and upcoming cybersecurity events.
AI-powered SOC analyst promises rapid, thorough investigations, 24/7 coverage, and scalable security outcomes for lean teams.
